by Lasse Scherffig
Introduction: There are no networks
At the heart of the Internet of Things lie protocols. They govern the way connected devices talk to each other and transmit data. They negotiate who is connected to whom. In his seminal critique of networking titled “Protocol,” Galoway demonstrated how protocols have to be read as both material and political, real and abstract, as they regulate physical connections and power structures: The Internet, according to this view, is a “political technology”1Galoway, A. (2006). Protocol. How Control Exists after Decentralization, Cambridge, MA, USA: MIT Press..
This political technology has, in recent times, increasingly been discussed as a technology connecting physical things. The Internet of Things (IoT) and ideas of ubiquitous computing mark a shift in the way engineers talk about the Internet, namely a shift from focusing on its abstract qualities (connections, routing) toward its real qualities (networked objects). The shift does not denote, however, a shift in the actual nature of the Internet, as it always has comprised both.
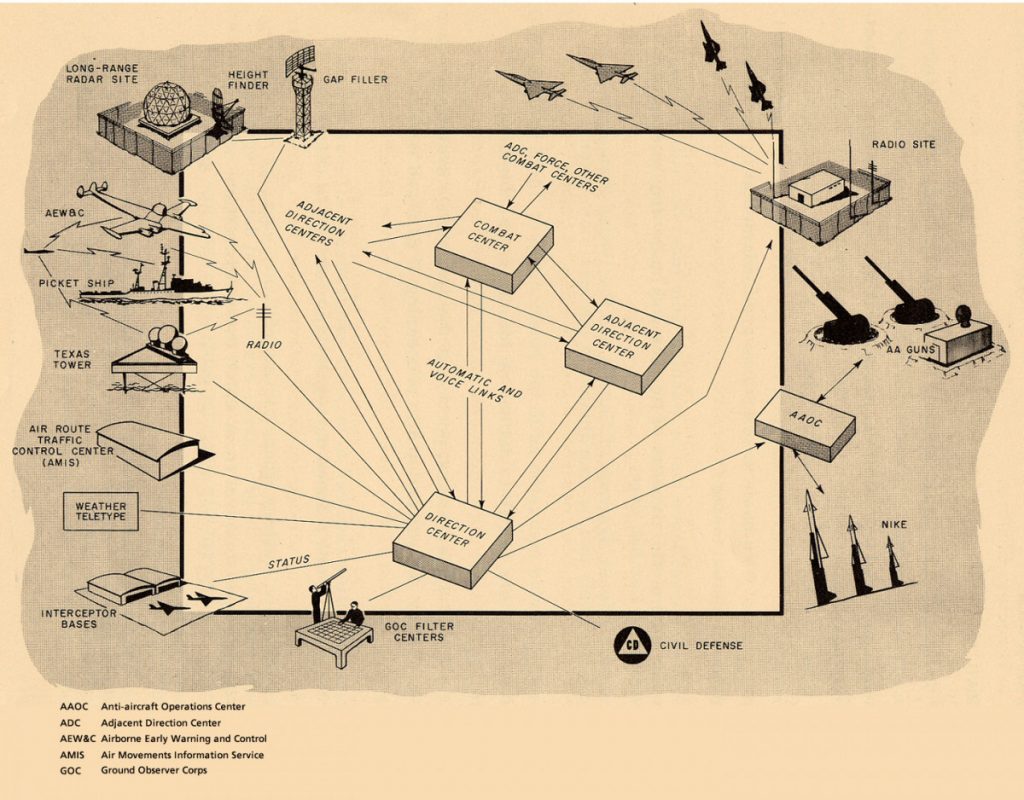
Historically, as soon as computers became interactive, they were connected to things. Whirlwind, the first interactive computer in today’s sense2Scherffig, L. (2018). There is no Interface (without a User). A Cybernetic Perspective on Interaction. Interface Critique, 1, doi: 10.11588/ic.2018.0.44739., was quickly turned into SAGE, the Semi-Automated Ground Environment air defense system, which already during the 1950s connected radar, weather stations, rocket launch sites, AA-guns, and even the cockpits of fighter jets. As a “precursor of the Internet”3McKay, J. (2004). A SAGE Intervention. Retrieved from: http://www.govtech.com/public-safety/A-SAGE-Invention.html, this network, therefore, has from the very beginning constituted an Internet of (military) Things.
The insight that the Internet always has been an Internet of Things brings to mind Friedrich Kittler’s famous dictum: “There is no software”4Kittler, F. (1995). There is no Software. CTheory, Retrieved from: http://www.ctheory.net/articles.aspx?id=74 . The idea of software, according to Kittler, only serves to obfuscate power relationships. In order to function and even to exist, software must always reside in the physical memory of a computing machine which also physically executes it. The very concept of software, according to Kittler, is merely a means of hiding that physical machine and its work from perception and control.
Similar things could be said about the Internet, and especially the “cloud,” an obfuscation which hides the means of networked publication and communication (including energy consumption), from view and access. The phones in our pockets are not only means of connecting to a worldwide network of information, they are also physical objects that are part of a highly complex system of connected things that collect data, consume power, and occupy physical locations. Contrary to the way the term normally is used we may, henceforth, understand the idea of an “Internet of Things” as a reminder of the fact that there are no networks. Instead, there only are material things and changing physical quantities in cables or the ether. It is time to make some of the consequences of that visible.
Layers and the ether
Abstractions, such as those that let us speak of software or the Internet, are not only a means of regulating power and access, they are a simple engineering convenience: Networking, for instance, is organized along layered abstractions, each of which free the engineers working with one abstraction from the tedium of understanding how the others work.
The bottommost layer of the famous OSI model that governs all networked communication today is the “physical layer.”5Wikipedia contributors. OSI model (n.d.). In Wikipedia. Retrieved from: https://en.wikipedia.org/wiki/OSI_model It regulates the physical transmission of raw zeros and ones over a communication channel such as a cable or radio waves. Higher layers organize how nodes in a network are connected, how information is routed from one node to the other without losing data along the way and, finally, how high-level applications seem to talk directly to each other. A video call over the Internet, for instance, happens on one of the higher layers that are responsible for establishing a streaming connection between two end-users, while blindly relying on the functioning of all the lower layers, down to the physical layer.
When we speak of the Internet of Things in the sense of connected objects and appliances, the physical layer often implies wireless transmissions. The protocols employed here vary from the Bluetooth standard and the cell phone GSM protocols to wireless networking or WiFi. Ultimately, they establish ways of connecting things to the Internet, through the ether.
The specifications defining the protocols of wireless networking are called IEEE 802.11. They define how, on the physical layer, bits are transmitted and received and how, one layer above the physical layer, these bits are directed from one device to another on a local network – via the medium access control (MAC) sublayer of the OSI model’s data link layer.
Data sent over the ether according to this specification is packed in datagrams that are called “frames.” These frames may contain actual data but may also be responsible for establishing and managing connections between, for instance, a WiFi access point and its clients – in other words, they regulate how things become part of the Internet.
In order for this to happen, clients must first find an access point to connect to. IEEE 802.116Wikipedia contributors. IEEE 802.11. (n.d.). In Wikipedia. Retrieved from: https://en.wikipedia.org/wiki/IEEE_802.11 provides two possibilities for this to happen: Access points may periodically broadcast “beacon frames” announcing their presence to every device in reach while clients may search for access points by sending “probe request frames” that ask for a specific network. From the point of view of the client the former method is passive and the latter is active. The name identifying a network in both conversations is its SSID.
Location, tracking, hacking
As a physical medium, radio is a local medium: its signals have limited reach and, especially the signals used by Bluetooth and WiFi, always imply a place at which they can be received. Not surprisingly, the importance of WiFi in establishing our contemporary technical understanding of location is significant. For instance, while navigation on a smartphone uses GPS, phones additionally rely on WiFi to establish location information. This is possible because according to the MAC specification, all WiFis not only possess a name (the SSID), but all access points also possess (at least in theory) a unique MAC address that is needed to send WiFi frames from one device to another.
By building a database of these addresses and their locations one can, therefore, infer a location by looking at which access points currently can be received. Both Google and Apple are working with such databases containing billions of location-tagged WiFi addresses, making localization on most mobile phones rely first and foremost on the local radio landscape.
Ironically, these giant databases are built and maintained by us. As we use our smartphones they constantly scan our surroundings for WiFi access points the locations of which, in turn, are uploaded to these corporate databases in order to enhance them7 Vaughan-Nichols, S. (2011). How Google – and everyone else – gets Wi-Fi location data. ZDNet. Retrieved from: https://www.zdnet.com/article/how-google-and-everyone-else-gets-wi-fi-location-data/. Our phones thus do both: using WiFi databases to fix their location and building these very databases.
MAC addresses, a simple low-level necessity to make the transmission of data between things over radio possible have become, therefore, the basis of a major part of today’s tech industry. Of course, they also are being used for tracking and surveillance. One of the many revelations in the documents leaked by Edward Snowden was that intelligence agencies experimented with collecting WiFi data at airports in order to track people via their phones8Weston, G., Greenwald, G. & Gallagher, R. (2014). CSEC used airport Wi-Fi to track Canadian travellers: Edward Snowden documents. CBC. Retrieved from: https://www.cbc.ca/news/politics/csec-used-airport-wi-fi-to-track-canadian-travellers-edward-snowden-documents-1.2517881.
This can be done entirely passively, by recording the probe request frames and the associated MAC addresses that identify the phones in an area. Such passive WiFi tracking has, similarly, been used in advertising: “Renew,” an advertising firm, has used trash cans in the city of London to track the phones passing by – until it was ordered to stop that practice9CBS (2013). U.K. bars trash cans from tracking people with Wi-Fi. CBS News. Retrieved from: https://www.cbsnews.com/news/uk-bars-trash-cans-from-tracking-people-with-wi-fi/. Because of this, hardware vendors have recently started randomizing MAC addresses to make tracking harder. The success of this, however, has varied10Martin, J., Mayberry, T., Donahue, C., Foppe, L., Brown, L., Riggins, C., Rye, E., & Brown, D. (2017). A Study of MAC Address Randomization in Mobile Devices and When it Fails. In Proceedings on Privacy Enhancing Technologies, 4, 268-286..
The only privacy measure that is originally part of IEEE 802.11 does not apply to mobile phones but only to access points. This is the capability to use “hidden” networks. These are networks that do possess an SSID but do not broadcast it and, therefore, do not show up on your device’s list of available networks, even if they are in reach. This measure could be called “privacy by obscurity” at best, as it only obscures the presence of a network to anyone looking at standard software, while technically these networks can still be identified. Even worse, it opens a set of different security flaws.
The reason for this is that if passive discovery of a hidden WiFi network is not possible, clients have to actively ask for them. This is why probe request frames are necessary in the first place. If your phone wants to connect to a hidden WiFi, it will repeatedly send probe requests asking for its SSID. In fact, depending on the operating system and manufacturer of your phone, it will also ask for WiFis that are not hidden, simply to make discovery of these WiFis faster. This means that anyone monitoring WiFi activity in an area will learn the SSIDs of some of the networks people passing through the area have used before. And, since SSIDs (together with MAC addresses) are tied to physical locations they are, in principle, able to learn where the user has been. Probe request frames, thus, constantly and quietly leak personal information. A notable project dealing with this in an education/activism setting is “Sasquatch” by Bonné11Bonné, B. (2014). Your Mobile Phone is a Traitor! Raising Awareness on Ubiquitous Privacy Issues with Sasquatch. International Journal on Information Technologies & Security, 3, 39-53. .
More importantly, perhaps, once your favorite network’s SSID is known, it can be spoofed in order to trick your phone into connecting to a rogue hotspot. This, in turn, allows for a variety of “man in the middle” attacks, ranging from data collection, password stealing, to attacks on encrypted communication12ENISA (2015). Passive WIFI Surveillance and Access Point Hijacking. In European Union Agency for Network and Information Security Info Notes. Retrieved from: https://www.enisa.europa.eu/publications/info-notes/passive-wifi-surveillance-and-access-point-hijacking. It has been rumored that there already are household appliances that contain rogue WiFi chips able to perform similar attacks – a maybe unexpected take on the Internet of Things as an Internet of “malicious networked flatirons”13Mathews, L. (2013). Chinese appliances are shipping with malware-distributing WiFi chips. Geek.com. Retrieved from: https://www.geek.com/apps/chinese-appliances-are-shipping-with-malware-distributing-wifi-chips-1575315/.
Where have you been?
If corporate and state actors can (and do) perform tracking and surveillance of connected things (and, by extension, humans) based on the protocols defined in IEEE 802.11, we can do the same. The work Where have you been? attempts to do this in an art context, providing an aesthetic access to leaked data by relying on a bricolage of corporate and community-based tools and technologies.
Using a Linux computer, a standard WiFi dongle, and open source software, it quietly listens to the probe request frames in an exhibition space. It then extracts the SSIDs leaked by these frames and tries to link them to geographic locations.

While the information stored in corporate WiFi location databases is valuable and, therefore, protected from malicious or creative access and misuse, non-corporate actors have established alternatives. Communities engaging in wardriving, the practice of scanning and mapping WiFi networks from a moving vehicle, have created large databases that likewise gather the locations of MAC addresses and SSIDs. Relying on that, “Where have you been?” can link the leaked SSIDs to crowd-sourced location information using the WiGLE.net database. As it runs, it also slowly builds its own database of locations its viewers may have been at, creating a tiny counter-database to those of the tech giants.
In a final step, the project returns to the APIs and aesthetics of the corporate Internet, making the leaked locations visible as Google StreetView vistas. On a screen or projection in the exhibition, it cycles through countless numbers of these views, providing a found footage sequence of seemingly unrelated places held together by Google StreetView’s characteristic and familiar aesthetics. Every now and then, however, within that stream it confronts you with a panorama of a place from your own past: a frequently used airport, a favorite café, your workplace, or your house.
Galoway14 Galoway, 158. notes that hacking (a term he uses broadly), implies “knowing protocol” and using that knowledge to “push protocol into a state of hypertrophy, hoping to come out the other side.” By adhering to protocol and taking it to its extremes, its (sometimes unintended), consequences may become tangible. In this sense, Where have you been? displays how the Internet (of Things) indeed is a deeply political technology. It makes apparent how connecting things globally through technologies that are inherently material and local protocols blur the distinction between public and private, establishing low-level negotiations of connectivity and high-level leaks of personal information. Relying on open source and community tools as well as the shiny surfaces of the corporate web, the work aims to uncover the cracks in the material foundations of our experience of a world of seamlessly connected things.