by Linda Kronman and Andreas Zingerle (KairUs Art+Research)
KairUs Art + Research1All our artworks and projects mentioned in this document are described in detail on our website: www.kairus.org artworks investigate the vulnerabilities of how network technologies are designed, used, and trusted. The works usually narrate episodes of investigations that derive from long-term research projects and we chosen to describe one of our methodologies as “artistic reconnaissance.” In this essay we explain how “artistic reconnaissance” is used to investigate network vulnerabilities, and how the careless use of IoT devices remains a global security and privacy issue. We also describe how “reconnaissance walks” in the South Korean smart city Songdo reveal an extreme contrast between the imagined and the real smart city experience.
Reconnaissance is exploration carried out to gain information. We have co-opted this exploratory military term of surveying a territory to outline a set of methods artists use to investigate infrastructures of power. As James Bridle’s artwork Watching the Watcher implies, tactics of military reconnaissance can now be reversed to expose military infrastructures and surveillance tools.2Bridle, J. (2013). Watching the Watchers. Retrieved from: http://jamesbridle.com/works/watching-the-watchers In Bridle’s work, US army reconnaissance drones are captured on publicly-available satellite imagery. In Ingrid Burrington’s work Reconnaissance the methodology is articulated in the title.3Burringron, I. (2016). Reconnaissance. NOME, Berlin. Retrieved from: http://sfaq.us/2016/09/reconnaissance-ingrid-burrington-at-nome-berlin/ Burrington uses pairs of before-and-after satellite images of data centers and military sites to investigate state and corporate structures. Using satellite maps, investigating leaked and publicly available industry or military documents, and investigating physical locations are common methods among investigative journalists and artists. Trevor Paglen, for example, does this in an outstanding way by tracking and photographing locations off underwater fibre-optic cables that the NSA probably tapped.4Jobey, L. (2015, December 31). Trevor Paglen: What lies beneath. Financial Times. Retrieved from: https://www.ft.com According to Paglen metaphors of infrastructure are often misleadingly immaterial:
“Infrastructures of power always inhabit the surface of the earth somehow, or the skies above the earth. They’re material things always and, even though the metaphors we use to describe them are often immaterial — for example we might describe the internet as the Cloud or cyberspace — those metaphors are wildly misleading. The Cloud is buildings with servers in them.”
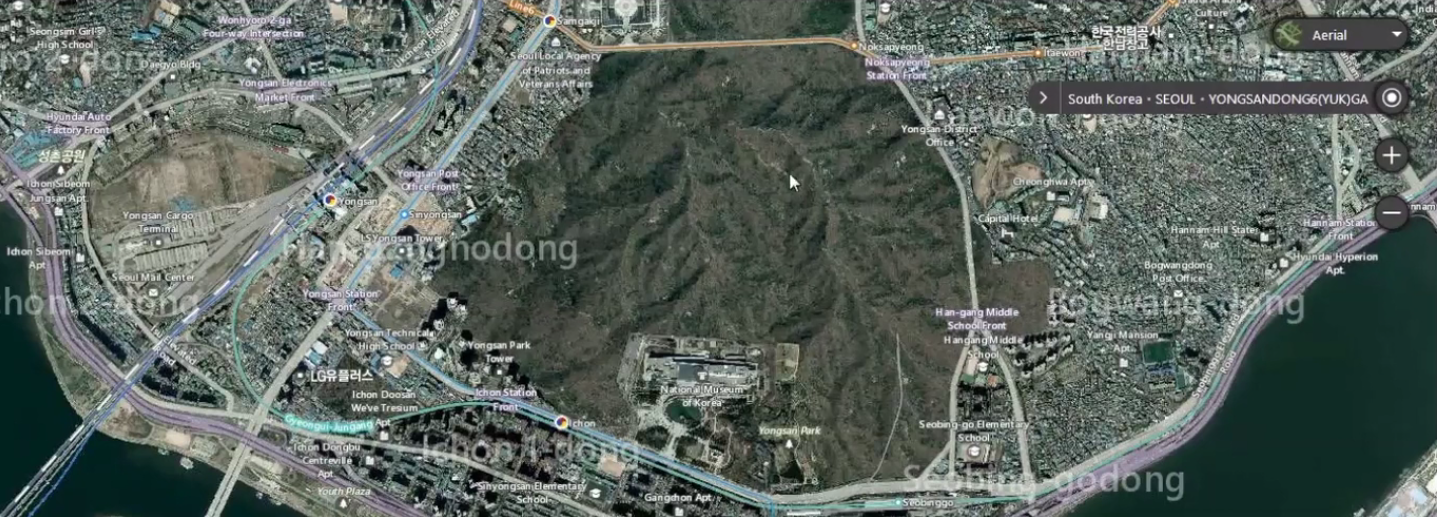
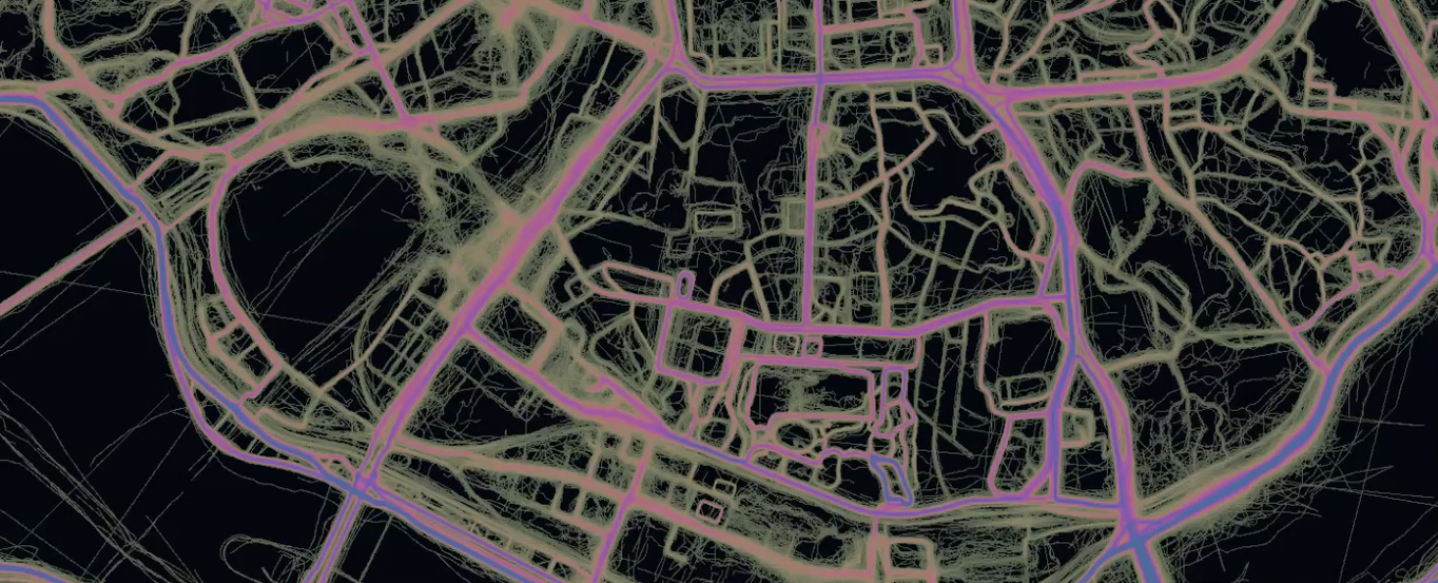
These investigations have revealed to us what the Internet or surveillance actually looks like. On the other hand they point our attention to what is hidden in plain sight. In our work Sharing locations: YONGSAN & HUMPHREY GARRISONS we used satellite maps from various mapping services to expose strategies of concealing, and exploring other layers of information like labels and heat maps of tracked movement. The work investigates two U. S. military infrastructures in South Korea; Garrison Yongsan and Garrison Humphreys. When military locations are explored through web mapping services such as Google-maps, Microsoft’s Bing-maps, Naver-maps, and Strava’s heat-maps we start to recognize differences in their appearance and how much information they reveal. It is not just subtle differences depending when the satellite images were taken, but attempts to hide the obvious: digitally disguised as parks, forests, farmland, or otherwise obscured and blurred.
By switching between various mapping services and their modes we start to unfold strategies used to hide these military infrastructures in plain sight. Consequently we start questioning what is removed from these publicly available imaginary objective representations and which policies are followed? Another layer of information is revealed by services using location based tracking. For example the Strava mobile app that is used to track athletic activities and share them on their social networking service. The app is compatible with several GPS watches and head units, including the devices US Army staff are equipped with. When Strava is used with default privacy settings, workout routes and personal times on activities such as running, cycling or swimming are logged and become available to third parties. When we share our locations with such services, satellites are not just recording representations of the earth in form of maps, data is also constantly recorded of how we move and behave. Combining the two enables informed reconnaissance of strategic sites.
Two videos in the Sharing Locations artwork show concealing strategies used by different mapping services at the U.S. garrisons Yongsan and Humphrey in South Korea. The parks, farmlands and forests are compared with activity movements that are shared by Strava network users. Anyone can log into the Strava social network. Once logged in, identities of individuals (including service members), and their present and past workout routines are visible to everyone, not just friends and followers. To further stress the exposure of personal data through the Strava social network as a part of the mixed media installation best individual lap times from each garrison are printed and exhibited on workout T-shirts.

Initially, reconnaissance referred to scouts or patrolling troops exploring enemy terrain. Technologies of machine vision such as satellite and drone images has been developed to assist the human eye. Further the term “network reconnaissance” used in cyber security context extends the terrain of exploration to include networked sensors, or as in our work Panopticities, the vulnerabilities of networked CCTV cameras. In this video installation city portraits of Seoul, Tokyo, Bangalore and New York serve as evidence of cameras that are insecure by design, accessible for both human and non-human intruders. By conducting virtual visits to cities through insecure camera lenses the artwork shows us private and public day to day activities and we get a glimpse of the rhythm of a city and its citizens daily routines: early morning commutes, busy lunch times at restaurants, evening cram schools, rush hours, or late night workout sessions.

Networked security cameras as part of the growing amount of connected devices also known as the Internet of Things offer 24/7 surveillance with integrated web-server allowing real-time processing and streaming. These web-servers are often insecure by design, meaning they are not protected by a password or have hard-coded login credentials saved as plain text. By default, the servers stream unencrypted data through publicly-accessible network ports, causing a potential risk of being intercepted and allowing unknown third parties unintended access to the cameras. Some manufacturers use the same vulnerable settings across their entire camera lineup. “By default, the Network Camera is not password-protected,” or “the default user name is admin” and “the password is 12345” can be read in the camera manuals. Besides insecure ip-cameras, modems and routers we found hundreds of critical infrastructure manufacturers that still use default and hard-coded login credentials.
Security cameras are supposed to offer security, not provide surveillance footage for anyone to view. Often, camera owners don’t realize that their cameras are accessible on the Internet with default insecure settings, enabling hackers to enslave these cameras into botnets. Malware will use insecure webcams to infect the rest of the often unsecured network, including routers and other devices in the “smart home,” threatening both the reliability of surveillance cameras and also serving as a transmission vector to attack other devices and critical infrastructure.

Whereas the two prior works use techniques of virtual observations made from a distance in the Ruins of the Smart City photo series we observe locally-tangible structures by documenting obsolete design implementations of South Korean smart city initiatives. South Korea is one of the rapidly developing, tech-driven Asian states, with the second fastest and most connected society in the world, when you look at average internet connection speed and active social media penetration. At the same time, it’s a very young democracy, everything is driven by the government and the market in a top-down approach, not focusing on the people who shall live in smart cities or use IoT devices on a daily basis. Cities like Songdo are built from scratch, supported by big tech companies amongst others IBM, CISCO, POSCO and LG. The photo series documents the massive investments in smart cities, its design, scenarios, and technology that are all hyped when a new city is planned. On the other hand, the built in technology often becomes obsolete or even dysfunctional during the process of building the city.
This is because the strategies of smart cities are inherently part of a consumer capitalism in which the new model must replace the old with an accelerating pace. This results in the envisioned smart technology being obsolete when implemented. As Nicholas Allen, Non-Executive Chairman, Link Real Estate Investment Trust5A real estate investment trust in Hong Kong., in a World Economic Forum panel admits: “Technology is changing so fast, that even if you put it in a year ahead of time the chances are that when you finish the building it is out of date.”6Allen, N. [World Economic Forum]. (2017, June 29). The Smart City Revolution: Where’s It All Going?. Retrieved from: https://youtu.be/mXtpdby9JSQ?t=53m35s Real-estate speculation, obsolete infrastructure and technology, coupled with the inability to attract new investment, result in an uneven development of the city. We have observed material traces of a smart city failures in form of empty malls, dysfunctional high-tech waste management infrastructure, and obsolete tele-presence technology. If we consider these spaces and technologies as contemporary ruins. According to Tim Edensor they offer: “opportunities for challenging and deconstructing the imprint of power on the city.”7Edensor, T. (2005). Industrial Ruins. Space, Aesthetics and Materiality. Oxford: Berg.
By investigating these sites we can start to challenge the sustainability as core concept of the smart city. For example in Songdo City there is a central pneumatic waste disposal system. Citizens can activate a smart trash bin with their ID cards and are then able to deposit their garbage in the bins. The trash gets transported at high speed through underground pneumatic tubes to a collection station where it is separated and recycled. The city wants to eliminate the need for garbage pick-up. During field research together with activists from Seoul-based Unmakelab, we were able to observe that the trash system is not working and piles of trash become part of the urban landscape. Residents living in the buildings that have invested in this infrastructure end up paying for a dysfunctional system. Due to examples like this, Songdo has been criticized as a prototype city or a test bed of technologies. For us, this shows that from a citizen perspective important questions to be asked are around the actually maintenance, openness, and sustainability of the technology that is promoted as enhancing the quality of life in the urban environment.
During these “reconnaissance walks” in the new smart city terrains we realized that the failed implementations of technologies reveal the materiality of the “smart city.” The technological development progresses so rapidly, specially from a city planning perspective, that 5-10 years later, many ideas they had been envisioned for Songdo are unpractical or not used by the citizens. For example, the tele-presence system praised in the Songdo advertising materials, that connects homes equipped with multiple screens with other homes or institutions such as hospitals or schools. This idea, developed before the breakthrough of mobile Internet usage, has left Songdo apartments full of obsolete screens in their kitchens, bathrooms and living rooms. Which city really needs a stationary video telepresence infrastructure now? Other observations included non-functioning sensors paved into the streets and lamp posts. In a smart city, recent history moves with such a great speed that a city still in construction can already feel as part of the contemporary past. It can be exiting to imagine the future city and the smart city always exists in the near future, as Thaddeus Arroyo, Chief Executive Officer, Business Solutions and International AT&T, reveals in his statement: “we are right at the forefront of another wave, with the advent now of the next generation of technologies… it is exciting to think what the future of smart city will be.”8Arroyo, T. [World Economic Forum]. (2017, June 29). The Smart City Revolution: Where’s It All Going?. Retrieved from https://youtu.be/mXtpdby9JSQ?t=55m36s Nevertheless, the visions of the future have not been realized as planned, at least in the case of Songdo. The photo series unveils the contrast between the 3D rendered imaginary Songdo and the real city which is a construction in progress and a ruin of a smart city at the same time.
In this essay we have described how we have co-opted tactics of reconnaissance to investigate vulnerabilities of the Internet of Things and smart cities. We have also identified how other artists use similar tactics in their artworks. We have demonstrated how these artistic reconnaissance tactics can be used to acquire evidence that problematizes the withstanding technotopian dreams of computing each aspect of our life. Networked devices and sensing cities will be part of our future. Rosi Braidotti, who explores the concept of posthumanism in her philosophical work, sees that we have become: “dependent on the enhanced capacity, on the enormous power that we get, power of connectivity through these device.”9Kirkham, S. (Producer). (2018, April 17). The human and the posthuman [Radio broadcast]. Sydney, ABC RN. Retrieved from ABC RN archive https://www.abc.net.au/radionational/programs/drawingroom/drawing-room-17.04.2018/9668486 According to Braidotti, we are in the preliminary stages of “an enhanced relationship to what these technologies make possible” and to get use to it, at the moment, we are suffering; Braidotti sees the price of the progress in terms of lost jobs, the anthropocene, and the digital proletariat and, therefore, calls for a transitional phase in which we take the positive and negative into account and make social plans to take care of the ones who risk being left behind. In a similar manner we recognize the benefits and dangers of becoming fully networked citizens and our artworks call attention to the vulnerabilities of technologies that should be taken into account when designing the programmable cities we are going to live in.